TACLANE Network Encryption
TACLANE - the most widely deployed family of High Assurance Type 1 certified encryptors in the world - has been protecting critical information and securing national security systems for over 20 years. Building on that legacy, the TACLANE portfolio continues to modernize and advance technology to protect against advanced threats of today and future proofing for tomorrow. Our proven and reliable TACLANE encryptors extend classified secure communications and information sharing from the tactical edge to the enterprise.
The Next Generation of TACLANE Encryptors

TACLANE-Nano is NSA Certified
The smallest, lightest HAIPE encryptor for mobile applications offers up to 200 Mb/s aggregate throughput and provides end-to-end secure voice and data protection.

Upgrade To The TACLANE-FLEX
With the same form and fit as the widely deployed TACLANE-Micro, the next generation NSA Certified TACLANE-FLEX provides advanced security features and scalable throughput (200 Mb/s to 2 Gb/s aggregate) to reduce the total cost of ownership.

New High Speed Ethernet Encryption
The TACLANE-ES10 (KG-185A), the first product in the TACLANE E-Series family of Ethernet Data Encryption (EDE) products, supports high speed Layer 2 network backbones in a ruggedized and low SWaP chassis.

MODULAR HIGH ASSURANCE SECURITY FOR THE ENTERPRISE
New TACLANE E-Series EDE Encryptors: TACLANE-ASP, TACLANE-ES100 (KGV-185B), and TACLANE-ES400 (KGV-185C) are designed to align and scale with IT ecosystems and requirements for next generation multi-domain battlespace.
THE TACLANE PORTFOLIO IS EXPANDING
We are developing innovative new encryption solutions, providing high assurance security further into the tactical edge and deeper into the enterprise. Learn more about our newest TACLANE products.
Our NSA Certified TACLANE Family of Network Encryptors
Certified to protect information classified Top Secret/SCI and below, the TACLANE portfolio extends from ruggedized, small form factor Inline Network Encryptors (INE) to high performance encryption platforms (200 Mb/s to 20 Gb/s aggregate throughput) and also includes a Non-CCI, Secret and Below CHVP. In support of the mission and the warfighter, TACLANE offers safe keying features (CDGSK and KMI OTNK) keeping warfighters out of harm’s way and Advanced Cryptographic Capability (ACC). The common GEM® One remote encryptor management, easy to use common interface, advanced technology baseline and features, superior customer support system and reliability is what makes TACLANE the largest deployed base of Inline Network Encryptors in the world.

TACLANE-Nano (KG-175N)
200 Mb/s
The Smallest, Lightest Certified HAIPE for Secure Tactical Communications

TACLANE-FLEX (KG-175F)
200 Mb/s - 2 Gb/s
Next Generation, Multi-speed, Customizable Encryption Platform

TACLANE Software
Agile VLAN, Performance Enhancing Proxy (PEP) & Trusted Sensor Software
Advanced Networking and Cyber Sensing Features for TACLANE Encryptors

TACLANE Universal Rack - Now on the TACLANE Approved Products List
The new TACLANE Universal Rack Mount Shelf Kit is easily installed in any IT closet to securely hard-mount a combination of TACLANE encryptors and power supplies using Quick Disconnect Accessory Trays.
LEARN MORE ABOUT THE TACLANE UNIVERSAL RACK
The TACLANE Universal Rack Mount Shelf Kit is just one of many ancillaries provided on the TACLANE Approved Products List (APL) - equipment specifically designed, tested, and validated by General Dynamics for use with TACLANE devices. Using approved products reduces risks associated with interoperability, redundancy, environmental factors and even warranty coverage.
Which encryptor is right for you?
Download our technical specifications spreadsheet to compare aggregate throughput, classification, size, power consumption, ACC compliance, and other features for our full TACLANE product line.
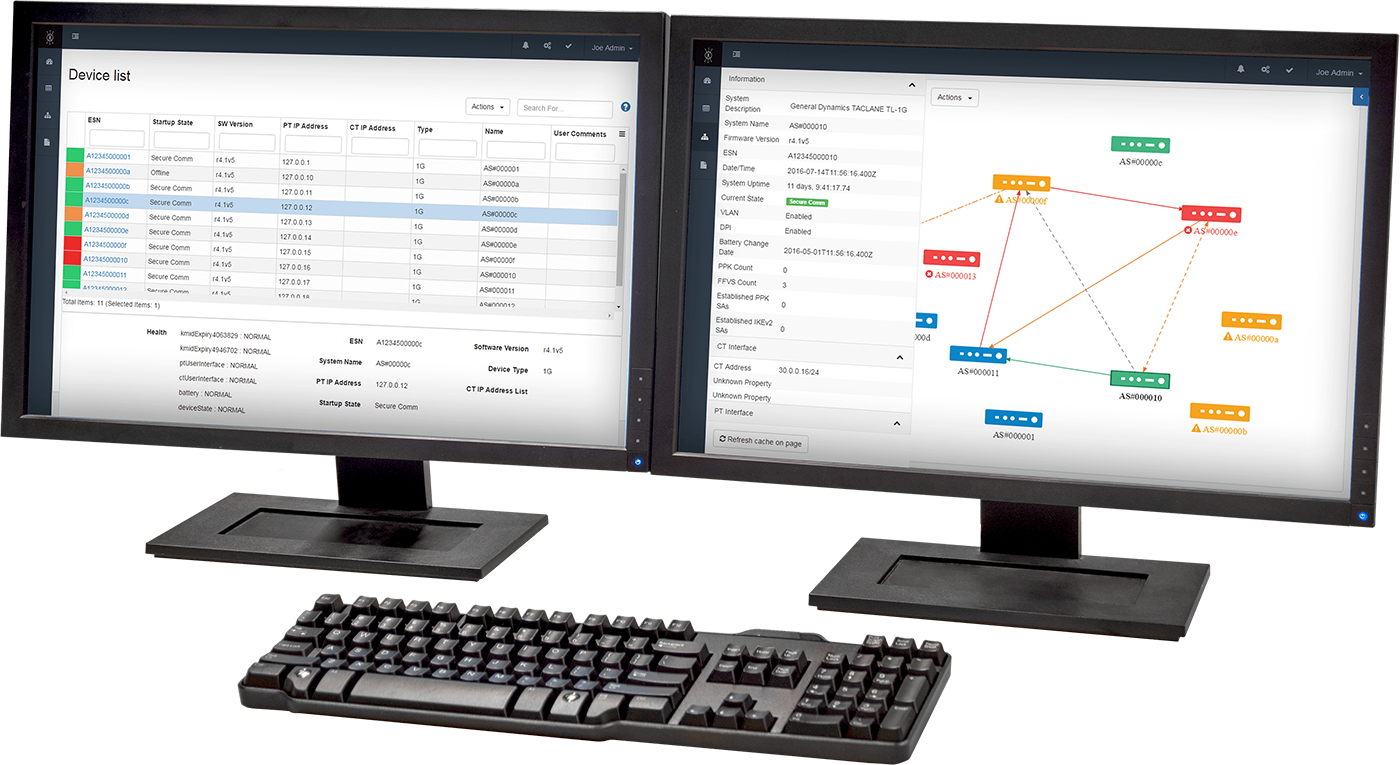
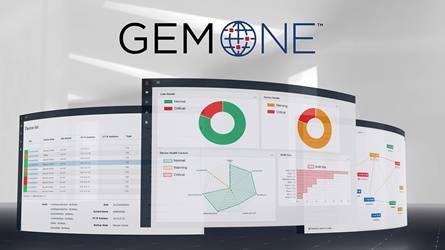
GEM One Encryptor Management
GEM One Encryptor Manager simplifies configuration, monitoring and management of a dispersed network of TACLANE INEs, Sectéra vIPer Secure Phones and ProtecD@R Multi-Platform (KG-204) Data at Rest Encryptors. The window to enterprise device management, the GEM One user interface is intuitive, customizable and enables faster decision cycles and alert response.
Type 1 Encryption Resources

ENCRYPTION SOLUTION RESOURCES
From whitepapers to webinars, and quizzes to test your knowledge, we have a library of technology and product solution resources to help you choose the right security solution for your mission. Topics include comparing key criteria between solution types like high assurance Type 1 and Commercial Solutions for Classified (CSfC) as well as networking technologies like the technology behind Layer 2 Ethernet and Layer 3 IP security.

TACLANE MISSION APPLICATIONS
Securing the mission from tactical edge to enterprise – the TACLANE portfolio of high assurance encryptors are NSA certified and approved for use in a broad range of applications. From small form factor embedment applications, to mobile platforms and kits, to command posts, tactical and strategic data centers and cloud security. Our team of Infosec engineers, account managers and product support staff are here to help you implement the encryption solution that's right for your mission.

TRAINING
General Dynamics offers a number of product training courses at our Annapolis Junction, MD and Scottsdale, AZ facilities. The courses combine classroom presentations and hands-on-exercises designed to teach customers how to install, configure, maintain, and use the latest secure products in a practical operational environment. Students who pass the short written and practical examination at the end of the course will receive a certificate.

You are never alone when you partner with General Dynamics to secure your critical information. With the largest deployed base of NSA-certified encryptors worldwide, General Dynamics is committed to support our customers worldwide with a 24/7 technical Help Desk.
For immediate assistance call 877-230-0236