PitBull Trusted Operating System

Secure Foundation, Strong Solutions
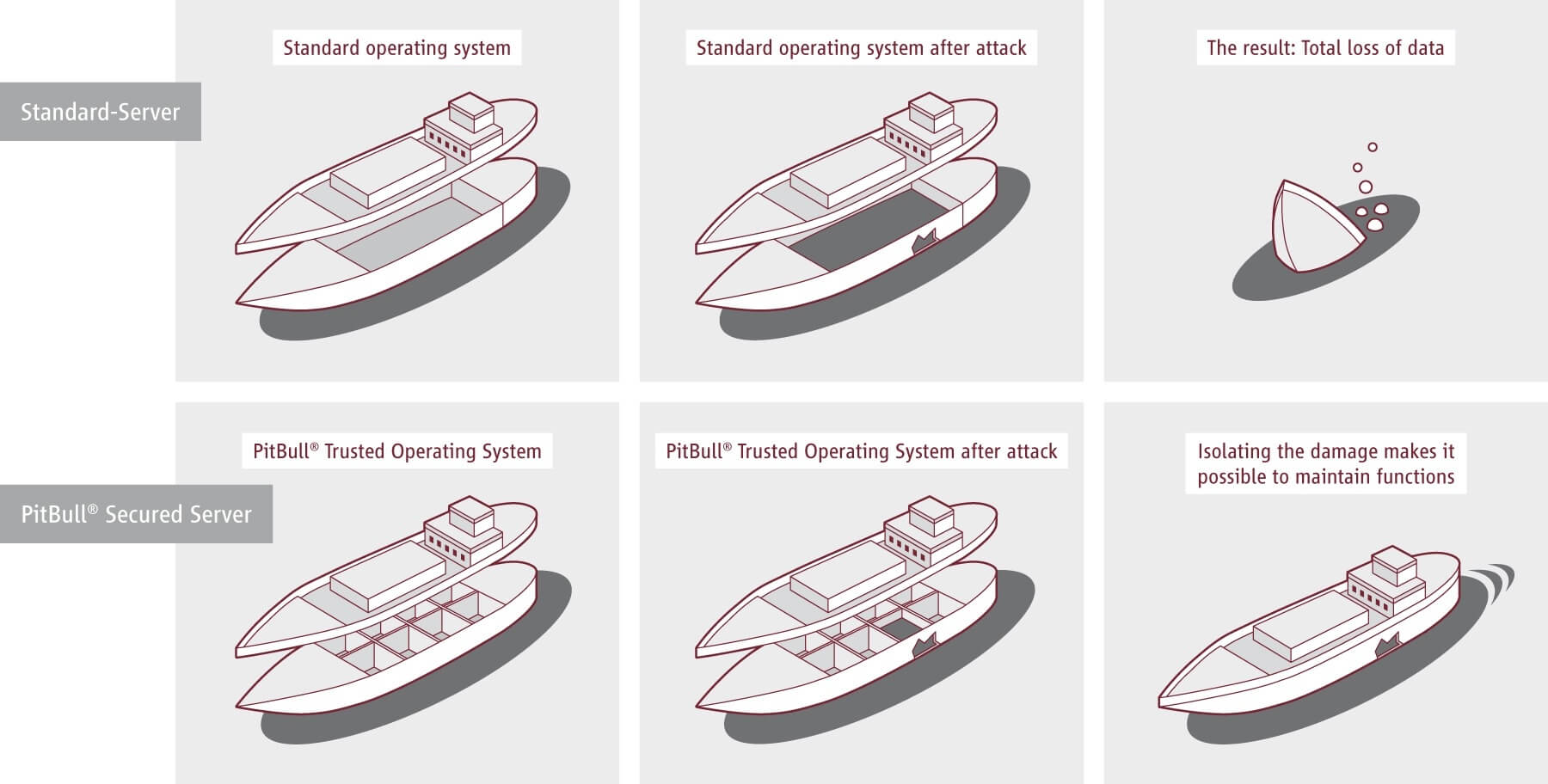
The PitBull® Trusted Operating System provides protection at the most foundational layer to allow you to develop systems, applications, and solutions with access controls and integrity throughout all levels. By securing at the foundation, PitBull avoids the need for added complexities – allowing you and your customers to be more efficient and to save on one-off security products. Enhance your solutions and lower cybersecurity risk by building on a flexible, adaptable, and secure operating system.
- Provides Secure Foundation for Applications
- Segregates Data, Applications and Interfaces
- Contains Data Loss and Prevents Data Spillage
- Reduces Insider Threat Risk
- Lowers Zero Day Attack Risk
Features
General Dynamics Mission Systems is partnered with security leader, QGroup. As a trusted operating system partner, QGroup integrates PitBull into their security solution offerings for international customers, including the German Bundeswehr. PitBull is also available as the secure foundation for customized solutions through value-added reseller Codeweavers.
- Adds a fundamental layer of security to ensure integrity for all levels of use
- Provides foundation for multilevel security
- Contains data loss and prevents data spillage
- Reduces insider threat risk
- Isolates applications, network interfaces, data, and users using simple security labels—does not rely on a complex rule set for isolation
- Prevents exploitation of bugs in any one application from damaging the entire system or other running applications
- Controls network resources usable by each application
- Controls and limits all user and administrator accounts—eliminates superuser vulnerabilities
- Allows for the development of flexible, ironclad security architectures
- Consolidates workstations, eliminating the need for multiple computing platforms
- Installs as an upgrade to an operational system
Additional Features
Security
- Identification and authentication
- Discretionary access control
- Mandatory access control
- Mandatory integrity labels
- Privileges
- Authorizations
- Security flags
- Auditing
- Integrity checking
- Advanced secure networking
Unique Features
- MAC and MIC lables supported at the kernel level
- Provides clearances for both users and processes
- Supports roles and authorizations
- Uses poly-instantiated MLS network ports and CIPSO-labeled packets
- Enforces two-man/four eye login authentication
- Allows for dual operational/configuration system modes of operation
- System integrity checks and integrity databases
Industry Standards
- Exceeds LSPP (EAL4+) Common Criteria requirements
- Provides Bell-LaPadula-based MAC (mandatory access controls)
- Supports the MTR-10649 MITRE Label Encoding Format file
- Supports Biba model MIC (mandatory integrity control) based labels
Software Development Kit
The Software Development Kit is included with the purchase of PitBull. The Kit includes libraries, header files, maintenance pages, and software developer manuals required to write PitBull-specific applications or modify existing applications to become PitBull aware.
Optional Security Features
Building on the PitBull Trusted OS, the optional security features below allow commercial and custom software to be easily configured into trusted, sophisticated network architecture, securing utilities, tools, and scripts. Other benefits include:
- Streamlines architectures, improves performance, and reduces costs and manpower requirements
- Allows users to securely access back-end applications via the Internet
- Enables a modular architecture tailored to a customer’s specific environmental requirements
- Secure Communications Enforcer: Tightly integrated trusted programs that pass packets between different security partitions. Examines each incoming request and, if validated, directs it to the appropriate service
- Security Gate: Trusted software component that mediates limited, secure communication between applications or utilities in separate compartments, without allowing direct access to each other’s files
- Secure Program Launcher: Allows users without powerful authorizations to execute programs that operate at a high level of security, but only in a limited predefined manner
Training
- PitBull Introductory Training (3-day): Introductory Training course covers all of the basic PitBull features and commands for users, administrators, software developers, and system architects
- PitBull Software Developer Training (2-day): Designed for software developers who will be writing software for PitBull or adding PitBull security features to existing software. Prerequisite: PitBull Introductory Training
- PitBull Advanced Training (2 day) (Coming Soon): Designed for administrators, software developers, and system architects; this course covers advanced topics and provides a more in-depth understanding of the PitBull system. Prerequisite: PitBull Introductory Training
- PitBull Web API Developer Training (2-day) (Coming Soon): Designed for software developers building client software to interact with PitBull-based servers. Prerequisite: PitBull Introductory Training
For more information about these classes or to enroll in an upcoming PitBull training class, please contact us at PitBullTraining@gd-ms.com.
Literature
- PitBull Trusted Operating System Datasheet [PDF]
- PitBull and SELinux Mandatory Access Control Systems [PDF]
- PitBull Executive Training Presentation [PDF]
- Using PitBull Trusted Computing Platform to Solve Real-World Problems Presentation [PDF]
- Protecting Data in a Modern Enterprise Solution Overview Presentation [PDF]
Get MULTILEVEL INFORMATION ACCESS & SHARING With TNE
General Dynamics Trusted Network Environment (TNE®) is the leading cyber edge solution in use today by the U.S. Department of Defense and Federal Agencies that enables multiple coalitions of interest (COI) to share sensitive information across security boundaries. Built on an enhanced Linux Operating System (OS) provided by our PitBull product, TNE enables this 360 degree collaboration with a suite of trusted software applications, utilities and tools that are fully accredited for cross-domain information sharing.